Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.
If you haven't heard of Hak5 products, they inspire a lot of passion. Hackers and pentesters love them for their efficiency and ease of customization. Sketchy VPN peddlers targeting the technology illiterate use their WiFi Pineapple to try to frighten people into buying dodgy VPN service. Even their cheapest option, the USB Rubber Ducky, has caused a lot of on-screen mayhem and shouting about being hacked by ducks, as can be seen in this intense Blacklist cameo:
Naturally, the infosec community was very excited to learn more about their new offerings. While rumor had it that at least two of the products were upgrades of previous devices, several hints throughout the week pointed to a new device entirely being launched. With that in mind, Null Byte reached out to Hak5 to see if we could get tickets to check it out, and I was delighted that Shannon got back to us!
The Launch Event
The venue was a small South Market restaurant in San Fransisco. When I pulled up, the line had already stretched around the corner, and security professionals were leaned up against walls chatting about the KRACK vulnerability. Everyone seemed excited to be there, and there was much speculation about the function of the new device.
When the doors opened, Shannon headed out to meet the crowd. Photos were taken, high-fives were given, and people entered the venue. The Hak5 team had really picked the right venue for their community of fans and tech enthusiast who attended, and the crowd was just enough that the environment felt more like a party you might throw for a group of close friends while keeping the energy level in the room high.
When the time came for the presentation, everyone crowded in close and listened. Darren Kitchen, Hak5's founder, took the stage and began to explain the details of the new products. We all expected to hear about the new Packet Squirrel, but Hak5 had made some interesting new changes to their lineup. I was particularly excited about the upgraded LAN Turtle that brings its own 3G network to the original LAN Turtle! Getting network access, but being able to avoid all the problem spots via your own network, is absolutely genius.

The Packet Squirrel
Of course, the star of the show was the Packet Squirrel. This tiny device is built for man-in-the-middle attacks. Literally. Its job is to sit in between a host and the WAN.

As you can see by the dime, this is a tiny device. It's small enough to be easily hidden just about anywhere. The lack of any markings or branding on the device makes it fit in as just another dongle in most environments. So what does it do? I'll let the Hak5 team sum it up.
The Packet Squirrel by Hak5 is a stealthy pocket-sized man-in-the-middle.
This Ethernet multi-tool is designed to give you covert remote access, painless packet captures, and secure VPN connections with the flip of a switch.
If the broad overview sounds good, the nitty gritty is going to sound great. The Packet Squirrel is a physically simplistic device — you get a USB storage slot, USB power in, an Ethernet in, an Ethernet out, a switch, and an indicator LED. This device is light on power, it can be powered for over a week with a decent USB battery.
The switch determines the payload state of the device, out of the box it comes with three payloads:
- TCPDump
- DNS Spoof
- OpenVPN
Of course, the payloads aren't set in stone. The Packet Squirrel allows the user to create their own custom payloads using PHP, Bash, or Python. The interaction between your custom payloads and the device takes place using Squirrel Script, which is not an actual scripting language, but rather a set of device-specific commands. There is also a community Git repo for grabbing custom payloads.

The TCPDump payload allows you to store PCAP files to your USB storage device for later use. The DNS spoof payload allows you to spoof DNS with ease, allowing an attacker to redirect a target to a fake version of a website.
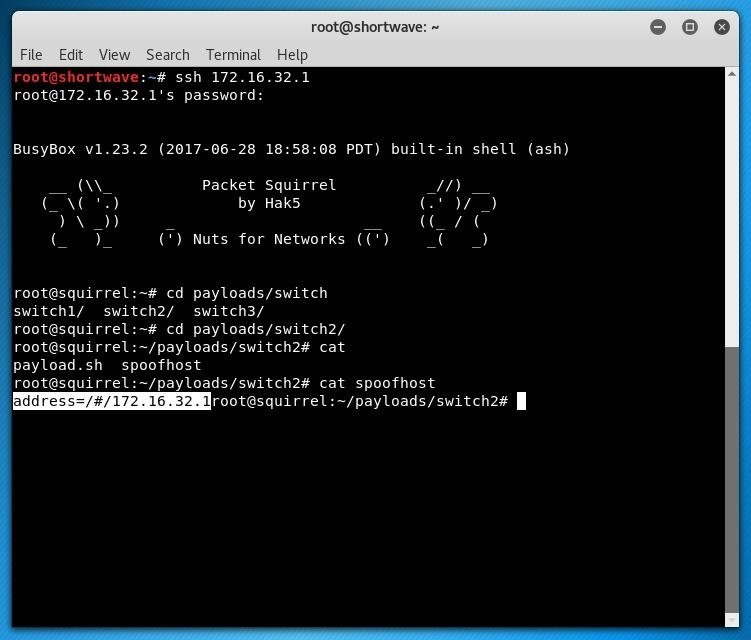
All it takes to get hacking is editing a simple config file on the device, and you're good to go! The OpenVPN payload allows for two different configurations; It can be used for remote access into the network via the Packet Squirrel or it can be used as a tunnel client.
As a tunnel client, the Packet Squirrel will ensure that all of your traffic gets routed through your OpenVPN compatible VPN of choice.
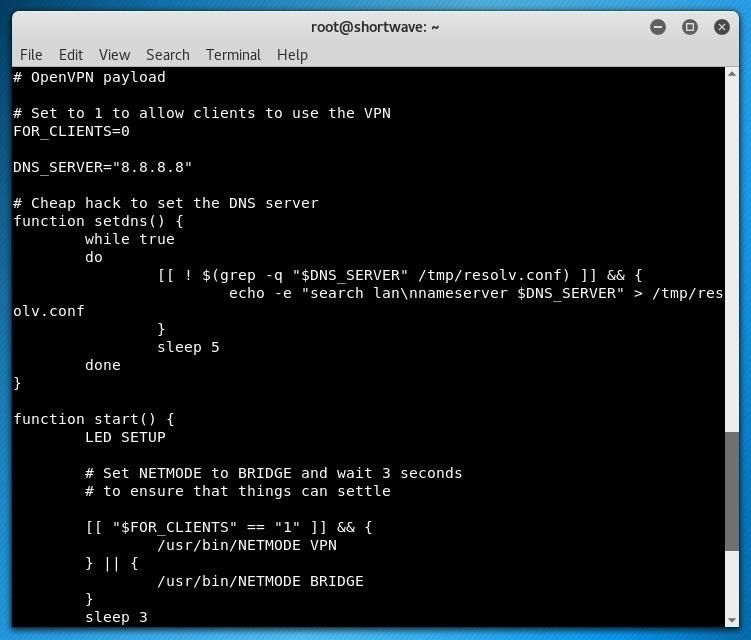
As with any Hak5 product, the flexibility and amount of options the community has to build on top of the Packet Squirrel is an exciting prospect. We're excited to see what projects the community takes on with these new tools. If the USB Rubber Ducky has been an example, community-inspired updates like new firmware will continue to add more exciting functions the Hak5 team may not yet have dreamed of.

Should You Get One?
The Packet Squirrel is an excellent network tool. It's exactly what I would expect from Hak5 — a tool designed to delight systems administrators, makers, and penetration testers. Like the entire Hak5 product line, the Packet Squirrel is a focused proof of concept that is well designed and easy to use.
If you haven't checked out the Hak5 product line, you're definitely missing out. Sure you could take a Raspberry Pi, or some other board and build many of these tools from scratch, but it'll take a bit of time away from learning about these security concepts. If your time is valuable, I'd say just buy the device for the job.

I know I'll be buying a couple more Packet Squirrels to hand out to less tech-savvy family members around Christmas. They may not be able to configure a VPN, or understand it, but with the Packet Squirrel I can just plug it in, check the LED, and know that it's working.
Thanks for reading, and to Hak5 for letting me check out the event! As always, you can leave any questions here or on Twitter at @0xBarrow. And don't forget to follow Null Byte and WonderHowTo on the social media platform of your choice:
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























1 Comment
these are neat. but you should also cover how to detect and disarm these as well!
Share Your Thoughts